The COVID-19 pandemic has created difficult challenges for businesses, and one of them is sending their team to work remotely. This is a challenge because many organizations are not prepared for the work-from-home set-up because of the lack of training, tools, and policies.
In addition, many employees are not equipped for remote work. Most likely they are going through a lot of change, uncertainties, and stress. Here are ways to secure your company as you deploy them remotely.
Focus on the most important risks that will create the greatest impact
Make the deployment process as simple as possible by focusing on the most important risks first. If there are additional things you want to add, please do.
Note that if the policies are too complicated, the less likely or the slower they will be implemented. The following measures are what we consider the top priorities of a company implementing a remote workforce.
A. Use Strong Passwords
One security breach to a team member’s computer could compromise the whole company. More than 80% of data breaches worldwide are caused by weak passwords, according to Verizon Data Breach Investigations Report.
Email accounts and website servers are the top targets of attacks to steal money and sensitive data. A hacker can break into company emails and execute bogus invoices and money transfers. Here are password-related behaviors that the workforce is advised to adopt:
1. Unique Passwords for All Accounts
Using different passwords for different accounts or devices is crucial for the simple fact that if one account is breached, the others won’t be easily.
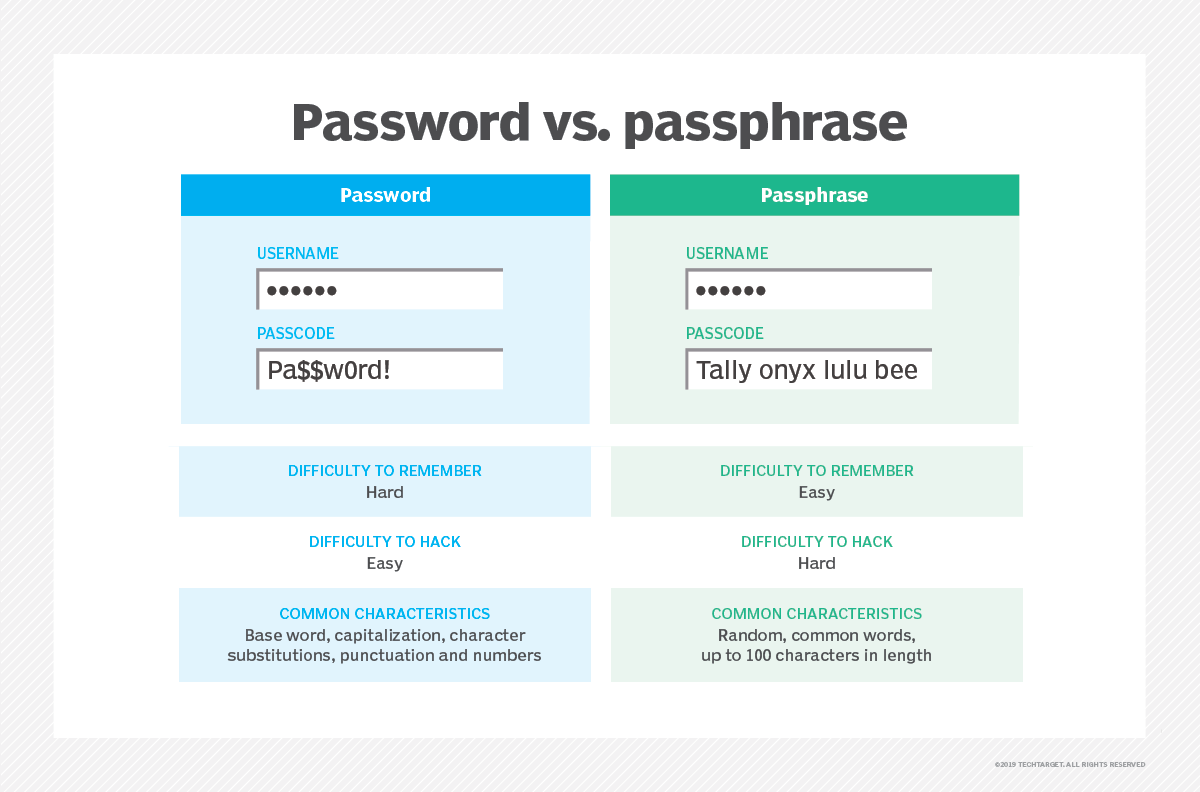
2. Strong Passwords or Passphrases
Passphrases may still be new to you, but this behavior is being promoted by cybersecurity authorities for quite some time now.
If you still get used to passwords still, make sure to use strong passwords while you gradually transition to passphrases.
To generate or store strong passwords, you may use password managers.
3. Password Managers
Investing in a good password manager is essential to preventing cyberattacks. Not only that it can help your company secure sensitive data, but it can also boost productivity as employees have lessened the burden of keeping a huge list of passwords, and have less worry about security liability.
You may also reach out to a third-party company to do cyber security assessment, training, and implementation.
4. Multi-Factor Authentication
Also called Two-Step verification or Two-factor authentication, an extra layer of security to access your account which requires you to enter (or do) a certain action related to:
- Something you know (like a birthday, or mother’s maiden name)
- Something you have (your phone, or security dongle)
B. Educate Your Remote Team About Social Engineering
In times of change and urgency, scammers take advantage of the situation by manipulating (or engineering) people for a certain action. Some examples of social engineering:
- Phishing attacks – pretending as another person or organization to get access to your accounts or financial assets. The most common form is email phishing.
- Phone calls or SMS scams manipulate people towards certain actions by pretending to be connected to you or a person of authority. Scammers commonly deceive recipients to send money or send sensitive information.
- Bogus social media account or fake news – an individual or a group can be socially engineered by spreading false information, or pretending to be someone else on the internet commonly known as “catfishing actor”, “posers”, or “trolls.”
C. Keep your Team's System Updated
Make sure that your team’s systems are updated. This keeps the system to receive new information including new cybersecurity attacks, spyware, and vulnerabilities.
D. Easy and Quick Incident Reporting
E. Secure WiFi Access Points
F. Use of VPNs
G. No Access to Family Members such as Children or Guests
Coordinate with key groups and create a 'Remote Work Advisors' Group
As you read through this guide, you’ll get the idea of what teams and resources to use depending on your culture and needs. Here are key groups to coordinate with:
A. Security Team
Work with your in-house or external IT security team to get a better understanding of what key risks are exposed.
- Identify behaviors that are at the top risks due to work-from-home.
- Don’t overwhelm your workforce with too many details. Make it as short as possible. Include additional items you feel are crucial.
- See this guide for our recommended top risks for remote work.
If you don’t have a dedicated security committee, you can contact us for a free security assessment.
B. Communications Team
After identifying key human behaviors that pose a security risk, work with your communications team to transmit and train your workforce. A strong partnership with the communications team leads to stronger effectiveness. Here are some best practices:
- Include a member of communications to your security team or vice versa.
- Motivate your workforce by emphasizing that these measures can also protect their family and themselves, not just the company.
C. Advisory Board
Set up an Advisory Board where significant members can input their feedback for the program. It can be a group conversation, a Slack channel, or an internal forum. You may also invite members from the Legal or Human Resources Department to share their input.
Create an Internal Channel to Manage Incidents and Questions
Set up a platform where you can quickly respond to security-related questions. Make sure that the team can use the system easily and approach the Remote Work Advisors quickly.
We highly recommend using a technology where they can get answers in real-time. In addition, ensure that only authenticated users can access that internal channel. As stated, this is to avoid overwhelming your Remote Work advisors so they can focus on staying vigilant. Here are our suggested technologies:
- Dedicated email alias
- Slack channel
- Facebook Workplace
- Or private-enabled forums such as Yelp
Ensure that the channel is not swamped or overburdened so it won’t give opportunities for password resets and social engineering attacks.